
31 Jan Why The Call For Zero Trust in 2022?
Results of Vanguard related Webinar discussion
1. What is best approach for talking to C-suite leadership about the importance of zero trust?
2. How are companies treating the importance of zero trust from a vendor perspective?
3. What validation should be applied for managing third-party vendor controls?
4. Is there a difference between an on-premises zero trust approach versus using zero trust with the Cloud?
5. Often employees will move to a different position or department within an organization, but their access and permissions fail to be updated. These transfers are usually quick and managers may not be aware of what permissions the new position comes with, and HR does not feel it is their job to correct such permissions. Do you have any recommendations for how to address this issue with a zero-trust framework?
6. It can be very difficult to monitor employee activity, as it requires going through highly detailed logs, which can be cumbersome. How can management be convinced that this is still important to do for company security and compliance?
7. What role does financial implications play in the event of increased internal threat?
The Environment
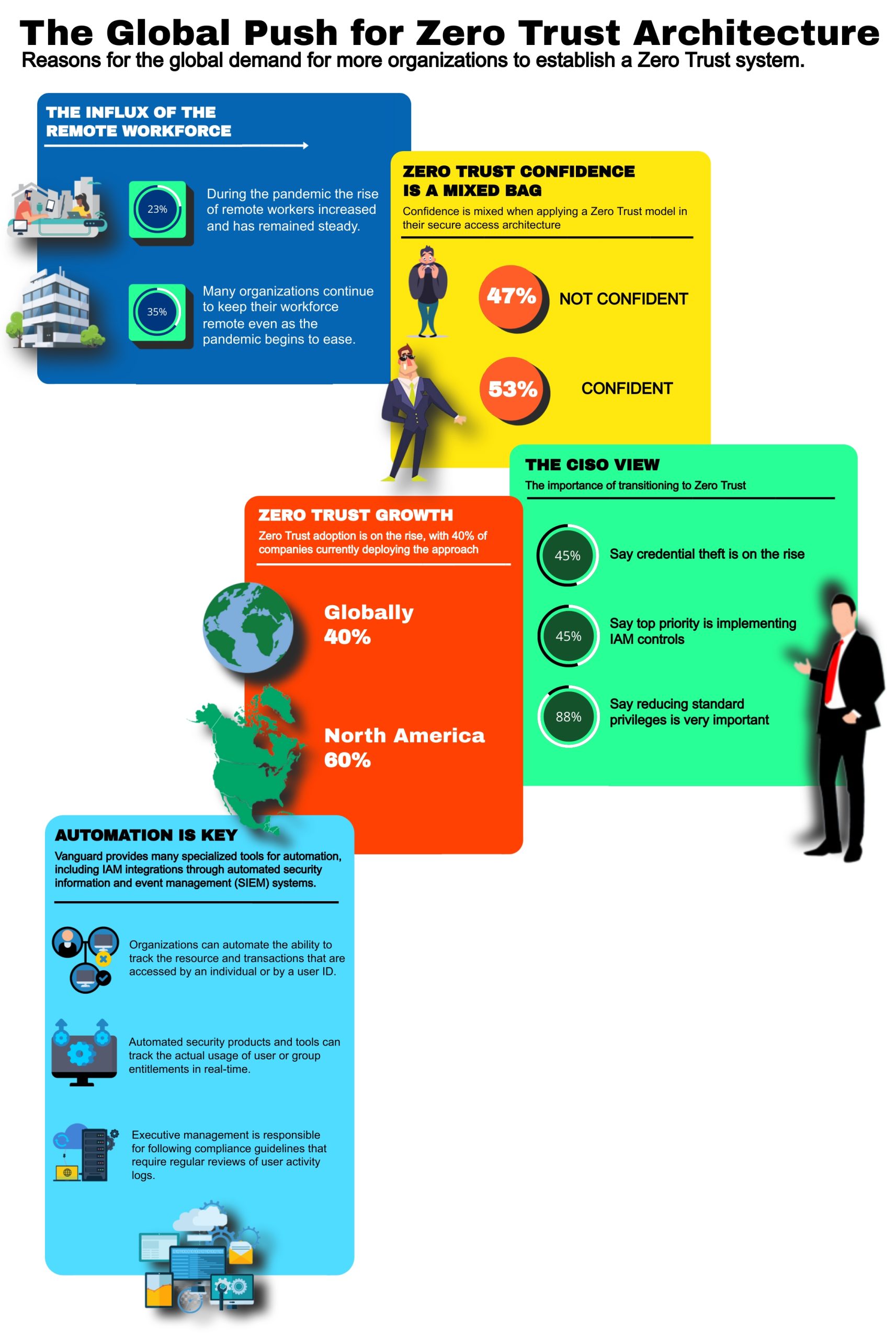
Increasing pressure on many organizations to meet compliance requirements has resulted in a push to adopt a zero trust approach. However, for zero trust implementation to be successful, enterprises must obtain a thorough understanding of the nuances of the framework.
Talking to C-suite Leadership About the Importance of Zero Trust
Zero trust is a paradigm shift about how people view security. One of the things needed to communicate back to your management or within the organization is that zero trust can actually automate a lot of the different data protections and governance requirements required of your organization from different, geographic locations, whether it is GDPR, the California GDPR requirement or data privacy requirements. Zero trust can aid in the process of achieving compliance with governance regulations and has the significant added benefit of ensuring better security for transactional activities within your environment.
The reality is, when it comes to approaching C-suite leadership, zero trust explains to them the fact that zero access will aid the organization in achieving better security as well as providing cost savings in the long-run. The biggest concern meeting with C-level members of organizations is that they want to make sure that they do not end up on the front page of a popular magazine or a newspaper article.
This is a way it’s a paradigm shift to ensure that the people are actually connecting to the system and those that are looking at data are the proper people to do it. It’s an idea where the organization has to pull together as a team and say, you know what? We really don’t trust anybody. You want to make sure that all the connections are correct and do everything possible as an organization to remove excess access. Understanding that one of the tenants of zero trust is the idea that individual access to enterprise resources is granted on a per-session basis.
Another idea in zero trust is that I trusted you last time but does not mean I trust you this time, and I will need to re-evaluate you and verify that you are a trustworthy person or transaction for a resource. There also needs to be trust that the person or transaction is coming from a location that has not increased the risk that you are now providing an attack factor.
A way zero trust can help an organization save money is that many countries around the world are actively working on data protection and data privacy and one of the biggest problems with data protection and data privacy is that it’s responsible for the proliferation of data inside and outside the organization.
One important thing to communicate to an organization’s management. Was it a good zero trust architecture that helped avoid data loss and avoid violating the principles of data protection and privacy rights of individuals by automating the process of ensuring the integrity securely?
Example: Let’s say you’ve got an individual within a bank or a healthcare institution, and they’ve got information that they need to send out, either within the organization or outside the organization. One of the things that zero trust can do is allow you to mark the data that you are sending with a sensitivity label. If somebody has information about my healthcare or my finances and they go to send an email or transfer the data, a zero trust architecture can look at that data before it leaves your organization and realize that the data contained has privacy or financial data included. In response, it will either refuse to send it out, ensure that it gets categorized properly, and will also ensure that it’s encrypted so that nobody else can get access to that data.
The difference between an On-premises Zero Trust Approach Versus using Zero Trust with the Cloud
The reality is when people ask a question like, should there be a difference between an on-premises zero trust and a cloud zero trust? What they are really asking you is this, should you be more suspect of the transactions and resources that occur in the cloud versus trusting what happens within your network? The answer to that question should always be no. You should trust nobody all the time. You should continually believe that. Do not ever believe that your network is secure, always believe that you have been penetrated and act accordingly. We have to realize that we need to defend everything the right away. There are people within your network and therefore you should not trust your own network more or less than any other network.
Not only is it people on the outside, it is people on the inside. Some of the biggest traces of data have been from people working in the organization. It was some guy named Snowden, who had an awful lot of information from those who had special clearances. There can be 35% to 40% of data that is ex-filtrated coming from an inside attack and it may be more than that because many organizations do not report it.
Role-Based Access Control and Employee Access and Permissions Failing to get Updated
These transfers usually take place quickly and managers might not know what permissions the new position should have. As people move within an organization, ensure that there is a defined role with entitlements, which match that user and their job functions as they move around. Entitlements can change frequently at some organizations. There are requirements and solutions available such as SOX (Sarbanes-Oxley Act) compliance, which requires a recertification of access on an annual or biannual basis. The utilization of automated products and tools to track the actual usage of entitlements and when or when an entitlement is or is not used by a particular individual or a group of individuals.
Organizations can automate the ability to track the resources and transactions that are accessed by an individual or by a user ID. These automation tools will tell whether a set of entitlements are no longer required, simply because that job function doesn’t require it or if that individual moved into a different job function and nobody thought about removing that particular entitlement.
Privileged Access and the Difficulty of Monitoring Employee Activity
Executive management has a fiduciary responsibility to follow the requirements of compliance guidelines. Almost every compliance guideline requires management to go through and review activity logs of users on an ongoing basis to look for suspicious activity and to review violations and respond to them accordingly.
Again, there are many automation tools available. Organizations will use the existing solutions they have in place. They just need to be convinced to use them in more automated and architectural fashion. In other words, everything’s going to blend together and work together to become a great way to take all of the logs from all the different systems, send them down to a single place for aggregation and correlation to look for those records that indicate a problem has or is occurring.
It is important for organizations to really understand, have they leveraged the products and tools that they bought? Are they getting the proper training? Are they educating the people that are using those tools correctly?
Learn from the mistakes of large organizations. For example, the Target breach in 2013. Target had a SIM in-house that alerted them to the fact that they had data leaving their organization. Some alerted them twice and their security operation center, based in India at the time, saw that, noticed it, and notified Target in the United States that there was a potential problem Target ignored the notification and the rest is history. Look at how much money that breach costed Target when they knew their own internal products were telling them that there was a big problem and that those products were evaluating the logs.
Organizations need to have the right people doing the right things, and that is the zero trust concept. Don’t trust anybody for anything and that’s really the paradigm shift.
Vanguard Integrity Professionals recommends a complete enterprise security assessment to pinpoint areas that need improvement and gaps that should be closed.



Sorry, the comment form is closed at this time.